What is SHA-512?
SHA-512, or Secure Hash Algorithm 512-bit, is a cryptographic hash function. It belongs to the SHA-2 (Secure Hash Algorithm 2) family of hash functions. These functions are used in cryptography, a field that uses mathematical concepts to develop secure information and communication techniques.
The Long Definition
SHA-512 is a cryptographic hash function that belongs to the SHA-2 family of such functions. To better understand this, we must first define a hash function.
A hash function is an algorithm that takes an input and produces a string of characters as output. This output is called a hash. It is usually of a fixed size.
As the name suggests, SHA-512 is designed to generate a hash value of 512 bits. The output size will always be 512 bits (64 bytes) regardless of the input size.
This hash algorithm has found applications in many areas. These include digital signatures, data verification, and password storage. Very few blockchain protocols use this hash function to secure their networks.

History of SHA-512
SHA-512 was first published in 2001. It was developed by the National Security Agency (NSA) and published by the National Institute of Standards and Technology (NIST) as part of the SHA-2 family.
The SHA-2 family is currently the most widely used family of cryptographic functions. It was developed in response to certain vulnerabilities found in its predecessor, SHA-1. In addition to SHA-512, the SHA-2 family includes SHA-224, SHA-256, SHA-384, SHA-512/224, and SHA-512/256.
However, continuous research and developments in cryptography have led to the creation of newer hash functions. The most notable of these is SHA-3, which was published in 2015. It is yet to gain widespread adoption. However, it is widely considered to be the successor to SHA-2.
How Does SHA-512 Work?
Hashing algorithms like SHA-512 are used to secure information. These can be messages being transmitted or data being stored. The algorithm takes the message, processes it, and produces a hash output. This hash takes the form of a string of characters of a fixed size.
Hash functions are one-way, meaning that they are irreversible. Determining the original output solely based on the hash value is technically impossible This is why they’re used for storing sensitive data like passwords.
Let’s look at an example:
Let’s say you create an account on a website that uses SHA-512. The platform will need to store your details, including your account password. This password will not be stored in its original form. Instead, the platform will first pass it through the hashing algorithm. They will then store the resulting hash function.
Remember, no one can guess the original password by looking at the hash value. This ensures that your account password is not exposed in case of a data breach.
This brings another question– How does the website know you have the correct password when logging in?
Well, cryptographic hash functions have another feature; they are deterministic. This means an algorithm will always produce the same output when the input is the same. So, when logging in, the password you type in goes through the SHA-512 function. The resulting hash is then compared to the one in storage. If they match, you have the correct password.
Note that all cryptographic hash functions generally work in the same way. What differs between them are the technical details. These include how the function goes about processing the input data and the size of the output.
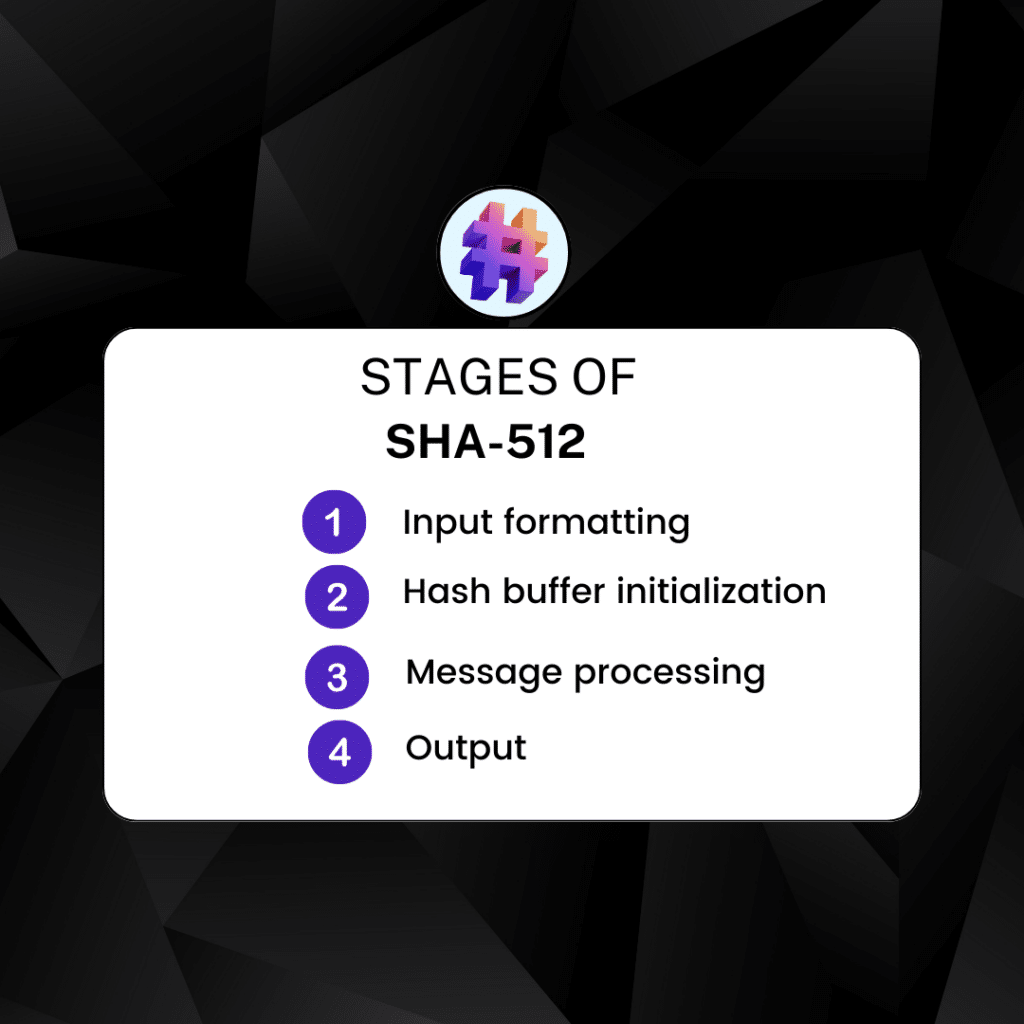
For example, with SHA-512, the algorithm starts by formatting the input. This involves converting it into a message with a combined size of 1024 bits or a multiple of 1024. This is because SHA-512 will process the formatted message in blocks of 1024 bits each. After processing, the function gives out an output. For SHA-512, the output is always 512 bits.
SHA-512 Applications
SHA-512 has several applications in information security. These include;
- Data Integrity: Similar messages will produce the same hash value when passed through a hash function. This feature allows SHA-512 to be used to verify the integrity of data. The copy of the data to be verified passes through the hashing algorithm and the resulting hash function is compared to that of the original.
- Password storage: As explained earlier, SHA-512 is used by some platforms to secure the passwords of their users. This application uses the same principle as the one on data integrity.
- Digital Signatures: SHA-512 can also be used during the creation and verification of digital signatures. When you digitally sign a message or document, a hash function is used to generate a hash of the signature.
- Cryptographic protocols: SHA-512 is used in many cryptographic protocols. These include secure socket layer (SSL) protocols, key exchange protocols, and Internet Protocol Security (IPsec) implementations. It is also used in a few blockchain protocols, although combined with other approaches.
SHA-512 Applications in Blockchain Protocols
SHA-512 isn’t the most popular hash function for blockchain consensus mechanisms. This is because it is a computationally intensive hash algorithm. It demands a lot of computing power, making it slower than alternatives like SHA-256. Therefore, the latter is typically favored by decentralized protocols.
However, there are some blockchains that choose to use it. They typically do so as part of a hybrid system that combines SHA-512 with other hash functions.
Stellar (XLM) is one such blockchain. The protocol was designed with the goal of enabling fast and cheap cross-border transactions. It uses EdDSA (Edwards-curve Digital Signature Algorithm) in its consensus mechanism. This particular implementation combines SHA-512 with SHA-256 to work.
XRP Ledger is another blockchain that uses SHA-512. However, it doesn’t use the entire hashing algorithm. Instead, it uses the first half of the algorithm. This is part of a consensus mechanism known as the XRP Ledger Consensus Protocol.
Want to join the Dypto journey? Follow our socials!