What is Cryptography?
Cryptography is the process of transmitting information in a format that people other than the intended parties cannot read.
The Long Definition
The term cryptography comes from the Greek word ‘krypto,’ which means secret. It roughly translates to “secret writing.” From this, we can derive the full meaning; transforming messages/data (encode) into a form that only the intended recipient can interpret (decode).
In modern terms, it’s the use of secure communication techniques. The goal is to ensure that data cannot be recognized and used by unauthorized people.
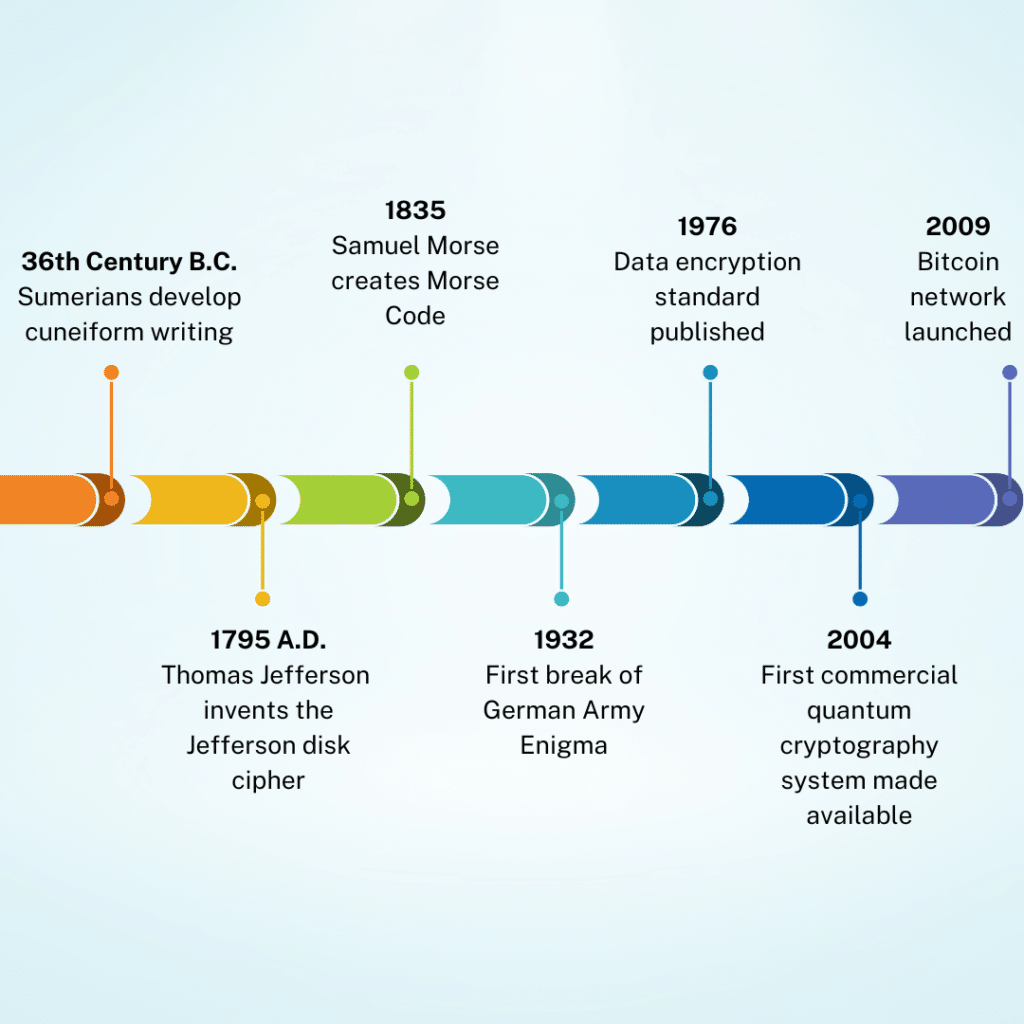
All in all, cryptography is a huge part of our world. It is used everywhere there is electronic communication – email, messaging, IoT (the Internet of Things) devices, DVD & Bluray, and electronic payment systems.
Perhaps the most revolutionary application is its use in cryptocurrency. In fact, cryptography puts the ‘crypto’ in cryptocurrency.
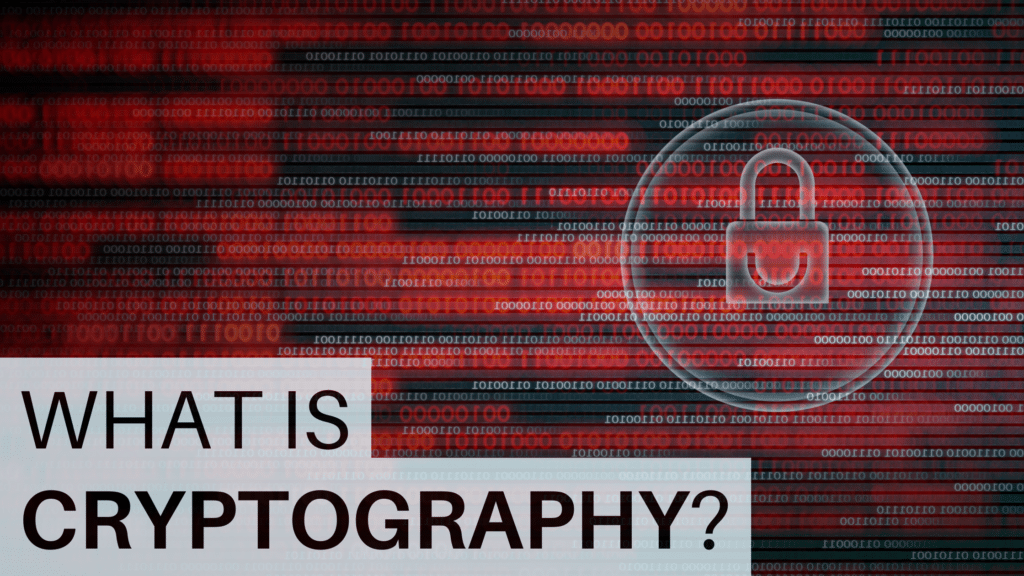
History of Cryptography
Cryptography has been used in many forms throughout human history. Ancient Egyptians hid information using hieroglyphs called micro dotting (substantially reducing the size of an image to prevent detection) and merging (combining two or more images).
Another example is the Caesar cipher used by the Roman Emperor Julius Caesar in his private correspondence. His method was to change the order of the letters of the alphabet by substituting the first letter with the fourth letter, the second with the fifth, and so on.
This form of cipher is known as a substitution cipher. For most of history, cryptographic techniques were substitution ciphers.
More advanced techniques came in the 20th century with the dawn of electronic communication. The two world wars inspired the invention of special machines to encrypt and decrypt data. A classic example is the Enigma machine, used by the Germans in World War II.
Computers helped push cryptography even further. As computers became more complex, so did cryptography. The internet created a need for even more advanced cryptography because of the need to secure worldwide communication and payment systems.
Modern Cryptography
Modern cryptography is as much a field of study as it is a process. It uses computer science and advanced mathematical concepts to encode and decode data. This is done following these basic principles:
- Confidentiality: No one other than the intended person can use the information.
- Integrity: The data cannot be altered.
- Non-repudiation: Neither the sender nor the receiver can later dispute the authorship or validity of the information.
- Authentication: Makes sure the data being claimed belongs to the right person.
The Role of Cryptography in Cryptocurrency
The link between cryptocurrency and cryptography is very strong. In fact, bitcoin’s whitepaper was first published on a cryptography mailing list in 2008. But, the idea of cryptocurrencies is much older than that.
It was birthed in the 80s by a cryptographer called David Chaum. He would go on to create the precursor to modern cryptocurrency, eCash, with cryptography at its base.
Every cryptocurrency since then – bitcoin, ether, ADA, Binance coin, and others, use cryptography. This protects them from double-spending and provides secure transactions. Additionally, it allows transactions to be anonymous and trustless.
The term trustless is a strange crypto jargon term that really means worthy of trust because you don’t need to trust a stranger, institution, or any other 3rd party in order for it to work). This allows cryptocurrency to be used without the need for a middleman (like a bank) and outside the control of a central authority.
The principles of cryptography are the same with cryptocurrencies:
- Integrity: Transaction data cannot be changed.
- Non-repudiation: You cannot reverse a cryptocurrency transaction.
- Authentication: The network knows who owns which tokens.
How Does Cryptography Work in Crypto?
Of the many cryptographic techniques, only two are used by cryptocurrencies. These are public-private key and hashing.
Public-private key cryptography
Public-private key cryptography.
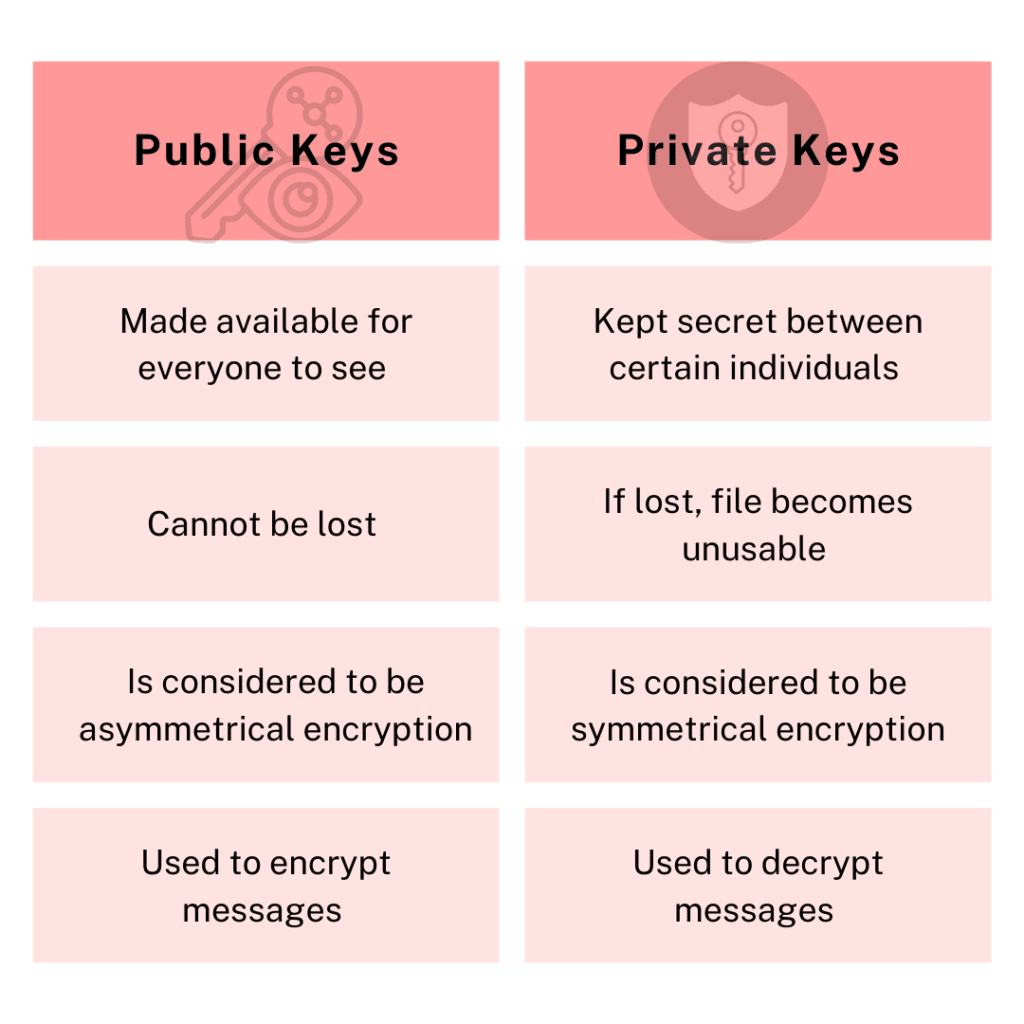
This is a cryptographic technique that uses two linked keys; a public key to encrypt the message and a private key to decrypt it. You can share the former with anyone you want– it is the wallet’s address. However, the private key needs to remain a secret.
The two keys are linked to each other in such a way that you can get the public key from the private key. However, you cannot get the private key from the public key. This is a cryptographic technique known as hashing.
The public key is obtained from the private key. Cryptocurrency coins or tokens associated with a particular public key belong to whoever has the private key When someone sends you crypto, they do so with your public key, which is linked to your private key.
So, as long as you have your private key, the network knows that the crypto is now yours. And whoever sent you the crypto cannot use it again since they don’t have the right private key.
This arrangement also allows for anonymity. All you need to do crypto transactions are the two keys. Your name, face, ID, driver’s license, or SSN are unnecessary.”
Hashing
Hashing is like a secret code that is used to check if a cryptocurrency transaction is real.
A lot of computers on the internet work together to agree if the transaction is real or fake.
They do this by passing the transaction through a special program that turns it into a secret code called a hash. If most of the computers come up with the same secret code, then they all agree that the transaction is real. This is called being in agreement or in consensus.
Additionally, hashing is used to make sure you can use your crypto wallet on different devices.
Want to join the Dypto journey? Follow our socials!