What is a Public Key?
In the world of cryptocurrency and blockchain, a public key is a unique string of characters generated by a crypto wallet’s algorithm. It is used to encrypt data.
The long definition
Crypto wallets work with the aid of cryptographic keys, public and private. Think of these keys as a digital lock and key used to lock and unlock data.
The public key, in this analogy, acts as the lock. It locks data in such a way that only the person with its corresponding private key can open it. This system works to ensure that unintended parties cannot do anything with the data.
This type of key is typically generated by an algorithm. It consists of a unique string of characters.
In the crypto world, public keys equal a wallet’s public address. Every crypto wallet has its own unique public key that serves as the address people use to send it crypto. The prefix public means that the key/address can be shared freely.

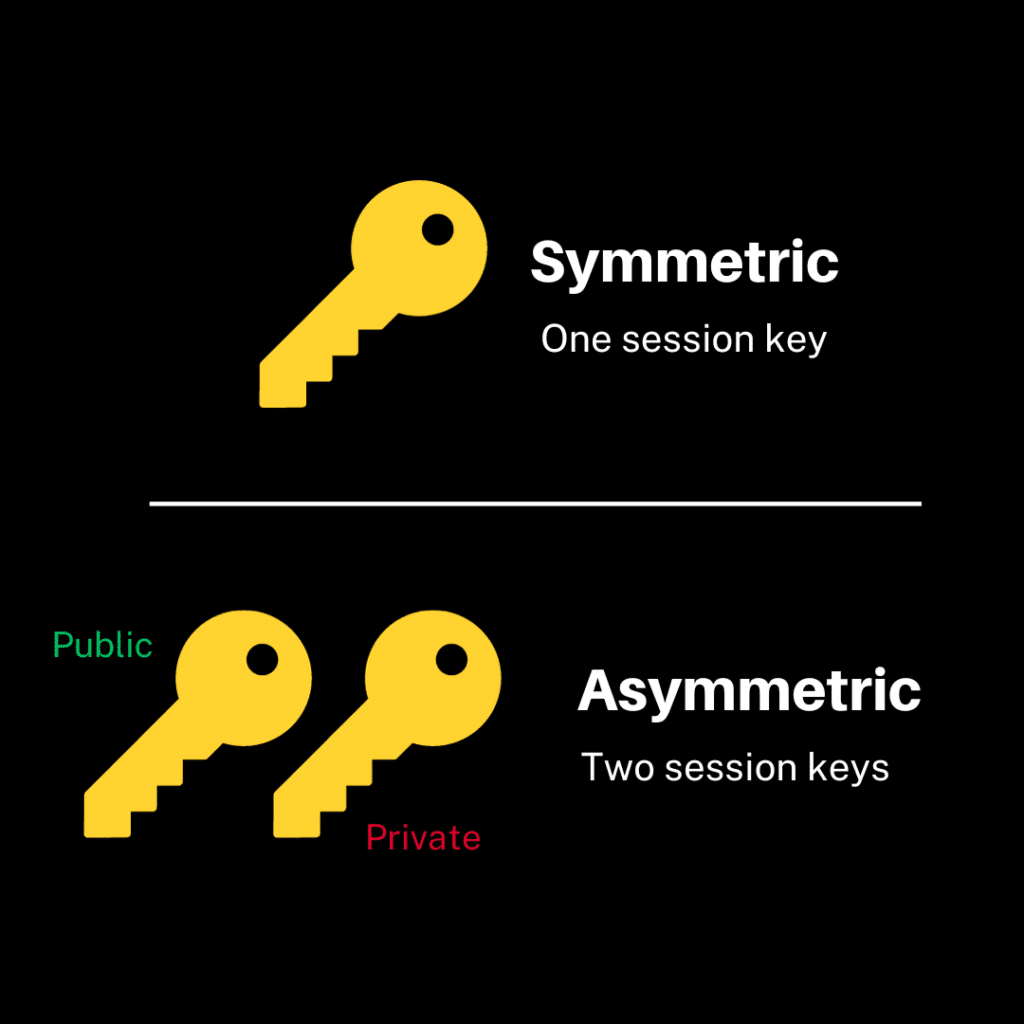
What is the Difference between Public and Private?
The public key is used to encrypt messages, while the private key is used to decrypt them.
The public key can be shared with anyone. In contrast, the private key is kept secret by its owner.
Public keys used in secure web communication are distributed through a certificate authority. The certificate authority verifies the owner’s identity, ensuring that the key is being used for its intended purpose. But in crypto, things are done differently.
How Do Public Keys Work in Crypto?
When setting up a crypto wallet for the first time, users generate their own pair of public and private keys right on their devices. There is no certificate authority to verify the owner in this system. Instead, only the person with the corresponding private key can send data (crypto assets) associated with the wallet.
When you initiate a crypto transaction, you use your private keys to create a digital signature that authorizes the transaction. Nodes and miners verify the transaction’s authenticity once it is broadcast to the network. They do this by checking the transaction data (public key, amount, recipient’s address, and digital signature). How?
Crypto assets live on the blockchain as bits of data. Each bit has a particular public key that it is associated with.
With this in mind, say you are sending 10 ETH to a friend. After you initiate the transaction, the nodes will first check that the digital signature is valid, i.e., matches your public key (or address). This gives them proof that the transaction was authorized by you, the owner of the public address. They’ll then check whether you have enough ETH (data) associated with your public address to cover the transaction amount and the gas fees required.
If the transaction passes all these checks, it is bundled with other valid transactions in a block and added to the blockchain.
How to Generate a Public Key
Generating public keys in crypto is easy. If you’re doing it for the first time, you just need to download wallet software like Metamask, Rabby Wallet, Trust Wallet, etc. The wallet will automatically generate a public key and its corresponding private key for you.
Note that public and private keys are linked such that you can use your private keys to generate the public keys. So, as long as you have your private keys, you can always use them to generate public keys. However, you cannot use the latter to generate the former.
